With cryptocurrencies, there is no centralized authority responsible for the security of your funds, while the dangers are abundant. Your wallet can be hacked, and your PC can be captured by a virus designed to steal bitcoins, you can make a mistake in the recipient’s wallet address and send money at the unknown address without the possibility of reversing a transaction, you can forget to make a Backup your hardware wallet, accidentally break and lose your encryption savings. It was reported that Bleeping Computer detected suspicious activity targeted at defrauding 2.3 million Bitcoin wallets, which they found to be under threat of being hacked. The attackers used malware — known as “clipboard hijackers” — which operates in the clipboard and can potentially replace the copied wallet address with one of the attackers. (Magas, 2018)
Fears aside, we are here to show you the ways that are best for protecting your cryptocurrencies. It is not that difficult if you know where to start. We will share some detailed advice on what you can do now to ensure the total security of your precious bitcoins. There are many ways to protect blockchain accounts from attackers.
Offline storage or wallet for the currency
One of the initial steps you can take to verify your Bitcoin wallet is to utilize cold stockpiling, otherwise called putting away Bitcoin values in an equipment wallet. This is additionally called the disconnected technique since it doesn’t require an Internet interface. This alternative isn’t so inclined to hacking. In any case, it is suggested that you don’t store numerous cryptocurrencies in chilly stockpiling; an ideal path is to isolate the Bitcoins into two fronts. The principal, which is a limited quantity, can be kept online for business purposes and, the subsequent sum can be put away in the equipment wallet.
Make backup copies of your wallet
Specialists are supportive of making backup copies to stay erring on the side of caution on the off chance that the gadget or information is lost. Backup is always beneficial when it comes to securing the data.
- You must make a backup duplicate of your whole wallet.
- It is vital to encrypt your backups, as resources stored online are prone to stealing. Even the computer system linked to the Internet becomes exposed, provided it is not appropriately protected.
- Use various locations for Bitcoin Wallet Data so you can recover your lost data effortlessly.
Add the second security layer with 2FA
Two-factor authentication adds the second security layer to your account. When enabled, you must enter a unique 6-digit password that only you have access to. These passwords change every 30 seconds, which gives hackers no chance to enter your account when trying random numbers.
Google authenticator and Authy are the best apps to protect important accounts. It is very easy to use.
Install the app from the play store or App store on Android/iOS.

Keep in mind that such services are more secure than SMS, as third parties can track telecommunication lines.
Log in to your exchange and look for the “Two-factor authentication” section. Usually, it is in security settings.
Scan the QR code provided in the authentication application on your phone to link it with your account. 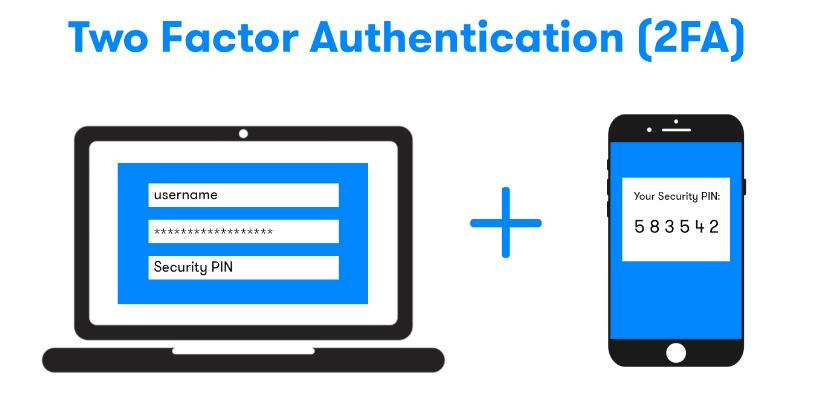
That’s all. Now, every time you log in, verify the authentication application to get a unique code.
However, do not think that 2FA is a magic pill that will guarantee the security of the funds, there are alternative solutions, and detailed instructions can be easily searched on Google.
In addition to your account in an encryption exchange, configure 2FA on all your online accounts that can be associated with your encryption savings in any way: your mailbox, your social media accounts, Whatsapp, Telegram, etc. Also, once 2FA is enabled, make sure it works properly before loading funds. The author of the article had a difficult night trying to access his account in Huobi until he discovered what the mistake was. Google Authenticate works a bit asynchronously when linked to Huobi, and the only way to break the 2FA is to write the sacramental code in a couple of seconds before it expires.
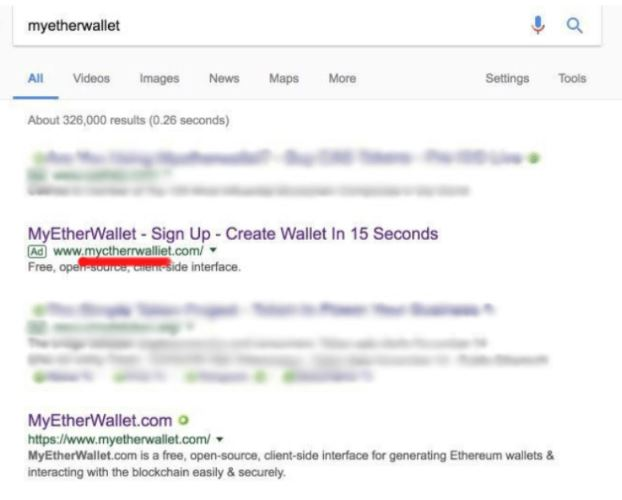
No ads, no phishing, no malware
Most hackers use highly tempting phishing ads for users to click on them and, once the user clicks on them, the ad will install malware on their system. Since it is difficult to distinguish between secure and malware-infected ads, we recommend installing an ad blocker in your browser.
Here is a list of ad blocker extensions that we have used personally and that we would also recommend:
- UBlock Origin
- Adblock Plus
As a rule, with or without an ad blocker, it is advisable not to click on any ads. Always!
Conclusion
There’ve been several high profile blockchain-related security breaches over the past few years, and many sounds like familiar versions of traditional computer security breaches. According to Emin Gün Sirer, an associate professor in computer science at Cornell University with expertise in developing cryptocurrency protocols and investigating blockchain security flaws, “the greatest security threat [to blockchain] involves targeted attacks on clients, as well as shared platforms such as exchanges.” Qualitatively, this checks out because attackers make cost-benefit analyses like any other individual, and they prioritize activities that will deliver the highest yield for the lowest effort investment. (Gupta, 2018) So, it is best recommended to protect not even your blockchain account but all other accounts. Once the accounts are hacked, the user might not get it back. The best we can do is protect it, so there is no chance of hacking anymore.
References
Gupta, R. (2018). Hacking into Blockchain: Is Blockchain Security a Concern? Retrieved from https://www.plugandplaytechcenter.com/resources/hacking-blockchain-blockchain-security-concern/
Magas, J. (2018). Six Tools Used by Hackers to Steal Cryptocurrency: How to Protect Wallets. Retrieved from https://cointelegraph.com/news/six-tools-used-by-hackers-to-steal-cryptocurrency-how-to-protect-wallets
Image by WorldSpectrum from Pixabay




